remote computer.
Notes -> Remote File Inclusion
11:21 PM | 0 Comments
remote computer.
Notes -> Remote SQL Injection
5:20 PM | 0 Comments
*Salau sql injection, ianya akan berlaku pada menu login untuk kita dapatkan username dan password
Remote SQL Injection
Ianya berlaku pada bahagian url @ address di mana kita akan "paste"kan injection pada text area url utk dapatkan username dan password
dimana:
username = plaintext
passwoord = hash (r7hy89p10) ::> yg x bole difahami
utk dptkan pswrd kita kena dapatkan md5 coder @ base64 coder
Notes -> XSS @ Cross Site Script
8:03 PM | 0 Comments
example: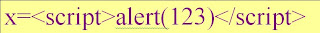
XSS berlaku pada ->
RFI berlaku pada ->
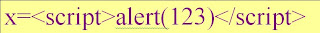
XSS berlaku pada ->
RFI berlaku pada ->
Notes -> Continue * SQL Injection
8:33 PM | 0 Comments
1. Kita gunakan if...else statement pada bahagian login
2. Escape from all single quote ('')
example:
Username : 1'or'1'='1
Password : 1'or'1'='1
$SqL="Select namapenyelia, tahap_penyelia, id_penyelia
from penyelia where username='$name' and password='$pass'
if($name="1'or'1'='1"){break;} ->mana-mana username yang ada "quote" kita reject
Tujuan if...else statement adalah untuk :
1.Check $name (variable) contain.
2.Reject kalau ada single quote.
Another way to protect your website:
1. Encrypt HTML files and hide source code
2. Disable content filters
3. Block website rippers
4. Customize HTML and add some effects
more info ->http://www.aerotags.com/products/tlp.php
Notes -> SQL Injection
12:06 AM | 0 Comments
Notes -> Maqic Quote
10:54 PM | 0 Comments
1' or '1' = '1
Happy Chinese New Year
11:59 PM | 0 Comments